enumerid - Enumerating valid ranges after initial compromise
In Summary : Enumerid works by querying the Domain Controller (DC) and asking for a list of RIDs for every Domain Computers in the enviro...
https://updatesinfosec.blogspot.com/2018/07/enumerid-enumerating-valid-ranges-after.html
In Summary :
Enumerid works by querying the Domain Controller (DC) and asking for a list of RIDs for every Domain Computers in the environment. It will then ask the DC resolve those RIDs to the clear text hostname. With this information, you simply perform a DNS lookup on each hostname.
DNS doesn’t check if you have access to the host in question. It simply resolves the IP address for you- therefore you are able to get a list of all currently leased IP addresses. All information is output into greppable format for easy parsing.
If the host currently has a leased IP, it will resolve. Otherwise the hostname will appear without an IP.
[...]
kindly refer the following link as follow up :
https://ift.tt/2KYzvHp
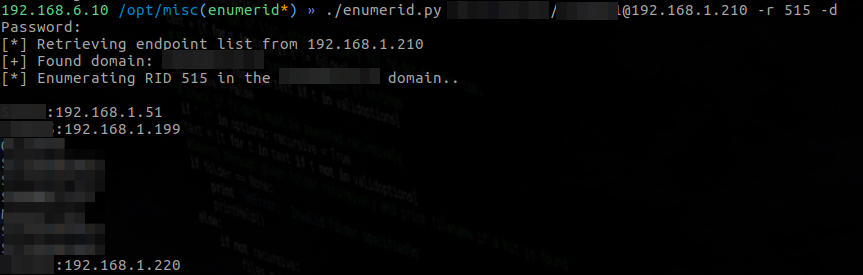
Enumerid works by querying the Domain Controller (DC) and asking for a list of RIDs for every Domain Computers in the environment. It will then ask the DC resolve those RIDs to the clear text hostname. With this information, you simply perform a DNS lookup on each hostname.
DNS doesn’t check if you have access to the host in question. It simply resolves the IP address for you- therefore you are able to get a list of all currently leased IP addresses. All information is output into greppable format for easy parsing.
If the host currently has a leased IP, it will resolve. Otherwise the hostname will appear without an IP.
[...]
kindly refer the following link as follow up :
https://ift.tt/2KYzvHp
