Finding Phishing: Tools and Techniques
In Summary : Phishing is still one of the most prominent ways of how cyber adversaries monetize their actions. Generally, phishing tries ...
https://updatesinfosec.blogspot.com/2018/07/finding-phishing-tools-and-techniques.html
In Summary :
Phishing is still one of the most prominent ways of how cyber adversaries monetize their actions. Generally, phishing tries to accomplish two primary goals:
kindly refer the following link as follow up :
https://ift.tt/2zqHWKy
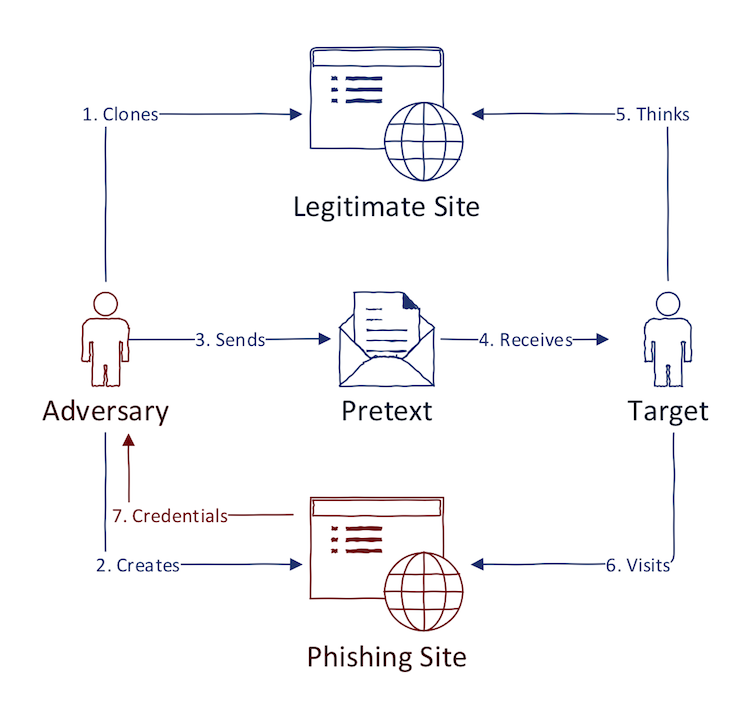
Phishing is still one of the most prominent ways of how cyber adversaries monetize their actions. Generally, phishing tries to accomplish two primary goals:
- Gain initial access to network - Adversary sends spear phishing e-mail with a well-crafted pretext and malicious attachment. Adversary then waits until the victim opens the attachment and connects to the C2 server. The attachment is usually one of Office file formats in combination with VBScript/WScript/Powershell and has pretty high success in evading anti-virus (when done correctly). [...]
kindly refer the following link as follow up :
https://ift.tt/2zqHWKy
